Posts Tagged security
Mac OS X makes handling SSH keys easier
Posted by Sébastien Stormacq in Apple, General, Mac OS X on 06/05/2014
I discovered something this Sunday morning that will make my day, week and month 🙂
If you don’t know much about ssh-agent or if you’re looking for a tutorial about using ssh public key authentication or ssh-agent, read one of the excellent articles linked from here before to continue here.
On OSX, Apple made it much easier to manage your SSH keys and to work with SSH, by adding two welcome improvements
- They added
ssh-agentto launchd(8) - They added
ssh-agentsupport for KeyChain
The first improvement alleviate user’s need to manually start ssh-agent for every session. launchd(8) will also makes sure ssh-agent is automatically restarted in case of crash.
Launchd configuration file is here:
hostname:~ user$ cat /System//Library/LaunchAgents/org.openbsd.ssh-agent.plist <?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple Computer//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>Label</key> <string>org.openbsd.ssh-agent</string> <key>ProgramArguments</key> <array> <string>/usr/bin/ssh-agent</string> <string>-l</string> </array> <key>ServiceIPC</key> <true/> <key>Sockets</key> <dict> <key>Listeners</key> <dict> <key>SecureSocketWithKey</key> <string>SSH_AUTH_SOCK</string> </dict> </dict> <key>EnableTransactions</key> <true/> </dict> </plist> |
But the best part is the second improvement : instead of storing your keys in .pem files in your ~/.ssh directory, you can tell ssh-agent to store your keys in the more secured KeyChain trusted store, as show on the picture below.
Apple silently added a -K option to ssh-add command to instruct ssh-add to store your SSH key in KeyChain in addition to loading the key in memory. ssh-agent will search for keys in their usual location on disk but also in Keychain.
What are the benefits of this?
There is no more need to explicitly call ssh-add when your session start, like you used to do in your .profile or .bashrc file. LaunchD will load ssh-agent and will instruct it to load keys referenced in your KeyChain. Note that the .pem file is not stored into KeyChain, you can not delete these from your file system.
Finally, because Keychain might synchronise across your machines through iCloud, your keys’ password are now available automatically on all your machines (provided you’re willing to keep a copy of your keys in iCloud – but that’s a different story)
Enjoy!
Using Apple’s XCode for open application development
Posted by Sébastien Stormacq in Apple, iPhone on 25/05/2012
When developing iOS application for jailbroken devices, you have to take care of many dirty details of application deployments on iOS. In particular, you have to take care of creating and registering your own development certificate, as detailed below.
This is where IOSOpenDev comes into the game, this packages a set of XCode plugins that automates most of this process. More than that : it also provides templates (aka empty project) to build your own Widgets, command line applications, SBSettings etc …
IOSOpenDev is a must use if you are serious about jailbroken app development on iOS.
But just for the sake of archiving – or if you want to do it manually, here is the process to code sign an application without using Apple’s provided certificate.
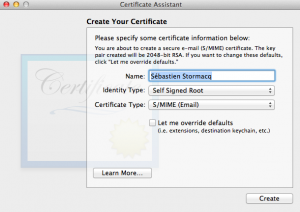
1/ generate self signed certificate using the Certificate Assistant in KeyChain Access application
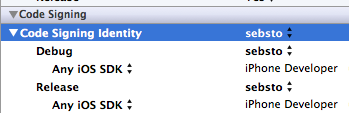
2/ tell Xcode to use that identity
3/ change XCode signature method (and restart XCode)
marsu:Contents sst$ sudo cp Developer/Platforms/iPhoneOS.platform/Info.plist Developer/Platforms/iPhoneOS.platform/Info.plist.orig
Password:
marsu:Contents sst$ sudo /usr/bin/sed -i .bak 's/XCiPhoneOSCodeSignContext/XCCodeSignContext/' Developer/Platforms/iPhoneOS.platform/Info.plist
marsu:Contents sst$ ls Developer/Platforms/iPhoneOS.platform/Info.plist*
Developer/Platforms/iPhoneOS.platform/Info.plist Developer/Platforms/iPhoneOS.platform/Info.plist.orig
Developer/Platforms/iPhoneOS.platform/Info.plist.bak
scp -r MyApp.app root@ip_address:/Applications
Web Services Security with OpenSSO Security Token Service (STS)
Posted by Sébastien Stormacq in Java, Oracle on 14/12/2010
 I recently experimented with OpenSSO Secure Token Service, one of the rare component Oracle will migrate from Sun’s Identity Management Suite to Oracle’s IAM Suite.
I recently experimented with OpenSSO Secure Token Service, one of the rare component Oracle will migrate from Sun’s Identity Management Suite to Oracle’s IAM Suite.
An Open Source implementation is also available from ForeRock’s OpenAM.
To summarize, a Secure Token Service is a third-party broker where Web Services clients can authenticate and receive a security token to be sent to a Web Service Provider. The Web Service Provider will, in turn, validate the token and to evaluate authentication and authorization decisions.
The best STS description / tutorial I found on the web is on a deprecated page of Microsoft’s MSDN. If you don’t know about STS, I highly recommend to read this serie of articles.
After installing / setting up OpenSSO / OpenAM, you will be ready to configure the STS part.
There are three approaches to interact with STS Server
Approach #1 – STS’s WSDL definition
This is the platform agnostic approach. Just rely on STS’s WSDL definition to generate whatever client code you will need.
Unfortunately, on Java SE 6, this approach fails because of incompatibilities in OpenSSO’s STS WSDL definition and JAX-WS.
ForgeRock’s community is tracking this issue under Bug ID 287 and Bug ID 306
Stay tuned on ForgeRock’s JIRA for more details on this approach.
Approach #2 : Using JAX-RPC and JSR 196 provider
JSR 196 is a SPI specification allowing to hook a filter inside a container. This filter will be invoked for all incoming and outgoing JAX RPC call, allowing it to be used for logging or security purposes for example.
OpenSSO and OpenAM do provide a JSR 196 provider for web service authentication (JSR 196) and authorization (JSR 115). This provider is able to work with an STS provider. The provider is available as part of openssowssprovider.jar JAR file.
While a little cumbersome to configure, this approach is working out of the box. As long as you strictly follow the documentation. These troubleshooting steps will probably be useful as well.
However, this approach has a major drawback : it is JAX RPC based, i.e. quite old, now that the (Java) world has embraced JAX WS. In other words, Oracle only supports this when the web service provider and the web service consumer are deployed into a GlassFish v2 instance.
So, if you want to use JAX WS, you will require a little more work.
Approach #3 – JAX WS
JAX-WS also provides hooks to intercept outgoing and incoming SOAP requests. These hooks are named “Handler“.
The good news about Handlers is that they are web-app specific, unlike JAX-RPC JSR 196 provider which are installed at container level; hence for all your web applications.
You can think of an Handler as a Servlet Filter, dedicated to web service calls. They can be part of a web app, to protect web services providers, or stand alone client, to protect web service consumers. IBM has a very good documentation about using Handlers with JAX WS web services.
To test OpenSSO / OpenAM STS service with JAX WS handlers, I suggest you to read this tutorial.
All in all, this is an excellent step by step article, covering deployment in Tomcat, GlassFish and Websphere.
Unfortunately, you will soon realize that these step by step instructions are not working.
Problem #1 : Oracle removed the download link to openssowssagents.jar file. Yes you read it right. As of today, there is no binary distribution for the JAX WS Handlers and WSS Agents. The JAR file is only available from ForgeRock.
Problem #2 : JAX-WS ClientHandler and ServerHandler are not included in openssowssagents.jar file. So even, if you are downloading ForgeRock’s JAR file, you won’t get these two JAX WS handlers.
So the only solution is to download the source code and built it yourselves. Building OpenSSO / OpenAM is not an easy task. This product has many dependencies and historical (legacy) branches. Anyway, your build will not be supported by Oracle nor ForgeRock. For your convenience, here is a openssowssagents.jar file with the JAX WS classes included.
Should you have a valid support contract with Oracle and/or ForgeRock, do not hesitate to open a support case and see what / if /how they will handle this situation.
Enjoy !
A Java library to use Belgium eID cards
Posted by Sébastien Stormacq in Java on 13/07/2010
Today, I used my Belgium Electronic ID smart card to digitally sign my Tax Declaration. Nothing new here, it happens now since six years in a row (I just wonder how many countries have setup such an end-to-end digital system, including digital signature, to interact with various administrations).
As every year, I wonder what API and libraries are available to programmatically extract or sign data with the smart card : a bunch of low level PC/SC API calls, a couple of Java-through-JNI samples, but nothing really high level and easy to use. Most of the examples returned by Google are quite old, not adapted to Java SE 6, not running in 64 bits mode and are not working on Mac OS X … sigh !
This year however was different, Google spotted eidlib, a Java SE 6 native library wrapping operations of the Belgium eID card.
This API is different from all the other I know : it uses the Java SE 6 javax.smartcard i/o framework to directly communicate with the card reader, exchanging APDU as required per the card protocol.
This is by far the easiest to use Java library for eID I found so far. You just need to include the JAR file into your classpath, then write simple code like :
BeID eID = new BeID(true); // We allow information to be fetched from test cards
// We fetch the information
System.out.println("InformationRetrieval -- ID information:");
System.out.println(eID.getIDData().toString());
System.out.println("InformationRetrieval -- Address information:");
System.out.println(eID.getIDAddress().toString());
System.out.println("InformationRetrieval -- Photo is saved to file:");
eID.getIDPhoto().writeToFile(eID.getIDData().getName());
Et voilà … ready to include strong authentication and signature in your own applications. I tested every example provided on the web site with NetBeans 6.9, using Java SE 6 64 bits on Snow Leopard.
This library was developed by Kristof Overdulve, at that time student at the University of Antwerp, for his Bachelor thesis. Kuddo !
[UPDATE]
Bart pointed me to this eID Applet project. If all you wanna do is include eID authentication or signature in your web application, then the eID applet is probably the way to go.
WS-Security with GlassFish ESB
Posted by Sébastien Stormacq in Uncategorized on 12/10/2009
When selling GlassFish ESB to partners, we (Sun) have to provide our partners with all the material allowing them a quick ramp-up on our technology. That’s the main reason why my group (Sales Engineers, Northern Europe) created a 3 days GlassFish ESB technical workshop.
My contribution to this workshop is a one hour module about WS-Security and GlassFish ESB (and OpenESB). The idea is to demonstrate how easy it is to setup a WS-Security enabled channel between a web service provider and a web service client.
Specifically, the screencast tutorial shows how to establish mutual certificate authentication between an EJB based web service and a JBI service assembly, acting as web service client, in this case, a BPEL module.
The module is now released online, booth as PDF slides and as a screencast tutorial.
To learn more about WS-Security, I recommend this reading.
Enjoy !
Next JUG Event : Java & Web Applications Security
Posted by Sébastien Stormacq in Java on 12/05/2009
The next YaJuG (the Luxembourg Java User Group) event will cover some security topics for Java developers :
- How to implement cryptography (encryption, key generation, signature, etc.) from within your Java applications
- A review of the Java top-10 security breaches in your web applications.
More details and registration are available online. Book your agendas : May, the 27th 2009